Realtime spatiotemporal matching
This algorithm is based on the paper “High Performance Spatiotemporal Trajectory Matching Across Heterogeneous Data Sources”.
Overview
The algorithm contains 3 important formulas to match heterogenous data feeds. These functions are:
- A similarity function reflecting the relatedness of two points.
- A Time Weighted Similarity (TWS) to reflect the temporal similarity between two sets.
- A Space Weighted Similarity (SWS) to reflect the spatial similarity between two sets.
It is possible for TWS and SWS to independently match a on different portion of the path, as shown in figure 5a from the paper, also shown below;
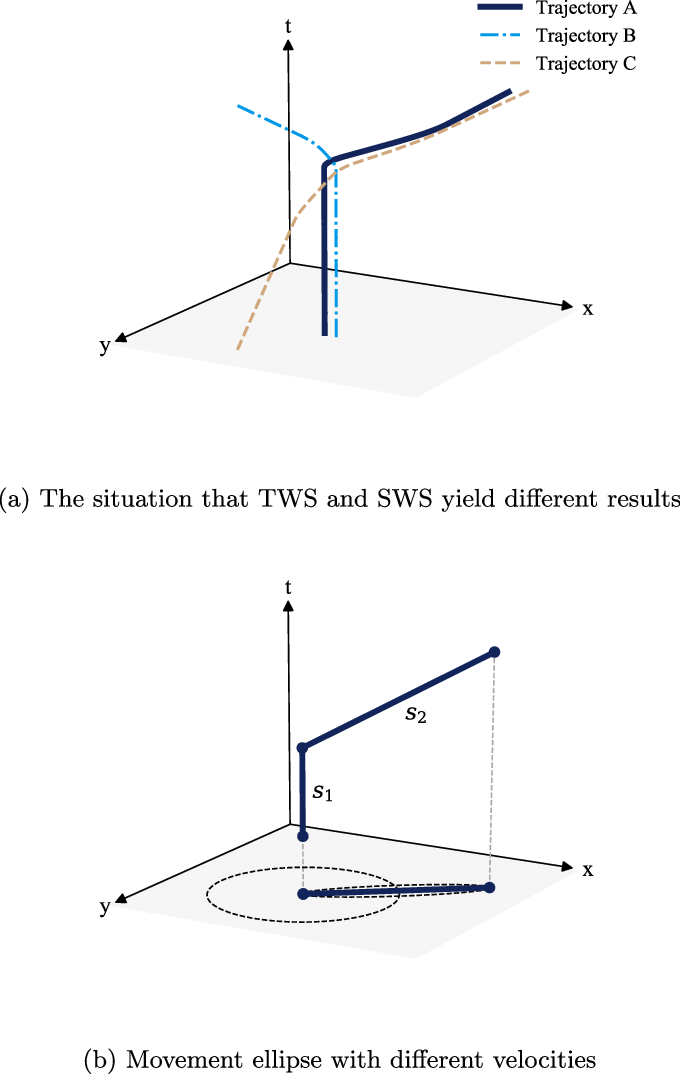
An important distinction between the similarity function and the TWS and SWS functions is that the similarity function checks the similarity between two points based on the euclidean distance and point variance. Though the TWS and SWS functions use the similarity function within, their task is to compare sets, instead of individual points.
The previous remark has the implication that this should be reflected within an implementation. As such;
- The similarity function should require individual data points as argument.
- The SWS and TWS functions should require sets as arguments.
- Similarity: A method calculating similarity of two points based on the Euclidean distance and point variance. Point similarity
- TWS (Time Weighted Similarity): A function calculating the similarity of two sets of points based on the temporal distance. Time weighted Similarity (TWS)
- SWS (Space Weighted Similarity): A function calculating the similarity of two sets of points based on their spatial distance. Space Weighted Similarity (SWS)